Meet Kanishk Sajnani. In is own words, he is a 20-something guy with no professional expertise, who hacks ethically, looks for no personal gains and believes that hackers should be rewarded for their positive contribution.
Sharing his experience on Medium, Kanishk penned down anecdotes from his hacking history that involves hacking Air India, SpiceJet, Cleartrip and more than a few other Indian websites. In his own words, he did that all in a month.
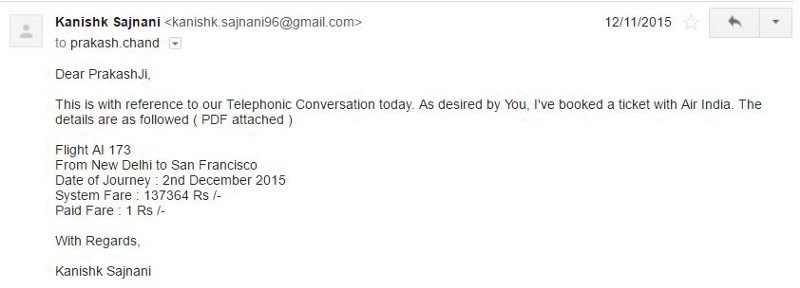
In 2015, he found a bug in the Air India portal and booked himself a seat on a US-bound flight for just Re 1. Yep! He could’ve travelled the world for free. But did he do that? Nope! Instead, he wrote them an email (on November 4, 2015), informing them about the bug. But a call was waiting for him.
On the 12th, he received a phone call.
Received an unexpected phone call from their Manager (Finance) on 12th Nov 15′. He asked me to prove if such a vulnerability existed & Oh boy! Did I?
In response to the call, he used the portal to book a ticket to San Francisco for just ₹1. Imagine that! Being debited a single rupee and getting the privilege to fly to USA. He could have done that if he wanted to. But his reason for hacking was ethical and as part of POC (proof of concept). He also sent a video for the same and a confirmation email of the ticket he had booked.
Air India were extremely grateful to him and even offered the internship he wanted. Kanishk did not take it up though.
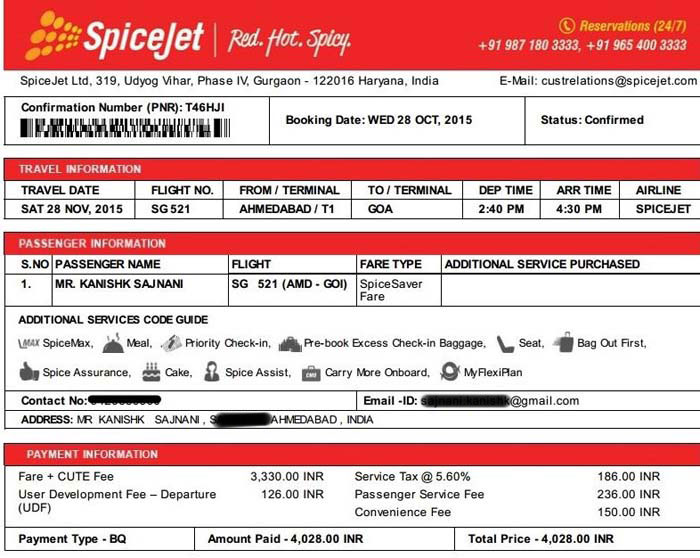
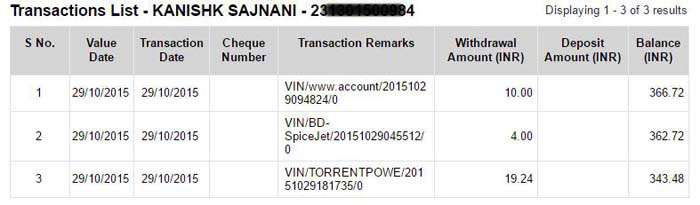
Then, comes the tale of SpiceJet. He found a “similar vulnerability in SpiceJet’s Mobile application” and informed them. On October 28, 2015, Kanishk booked a ticket to Goa from Ahmedabad which was worth Rs 4000, but he actually paid Rs 4 for it.
He brought this thing to SpiceJet’s notice as well and told them the loopholes in their app. While he was clear on how he wanted to help them out, their reply seemed extremely confusing.
“I decided to drop a mail to some senior Official. Shockingly, I wasn’t even able to find out the email addresses of their CEO or CTO or CMO. All I could manage to find were these ( custrelations-nodalofficer & apppelateauthority@spicejet.com) With no choice left, I sent a similar email ( like one to Air India) to SpiceJet too. Their reply baffled me.”
He even exchanged mails with their GM, Mr Pradeep Shah, who asked him to forward the other mails that contained details of the problem. Kanishk obliged and this is what he got in reply.
“They sent me our previous correspondence in a .eml type file attached *Double Facepalm * This time the mail was signed by their Nodal Officer. Either they didn’t understand the point I made Or they didn’t like to acknowledge the fact that their security was compromised.”
The ticket was valid still but Sajnani cancelled it himself on November 21. The cancellation mail didn’t mention any refund amount. So, he called up the helpline and was told that he was eligible for a refund of Rs 2000, which can be credited to his account or could be used on his next trip. His observation? The financial systems’ back-end couldn’t detect irregularities in payment.
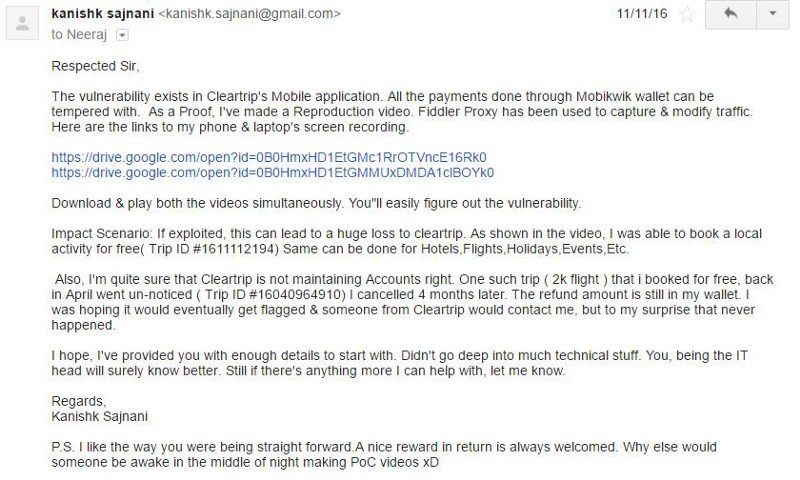
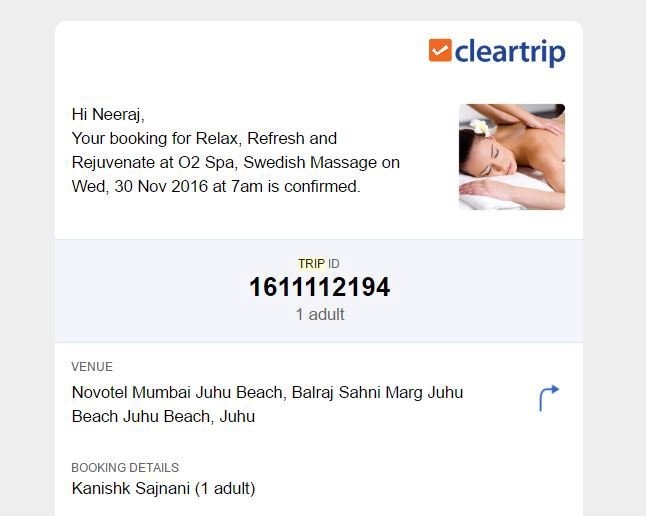
The next portal that he found to be extremely vulnerable was Cleartrip. An App he could have used not just to book flights, but ‘hotels, trains, restaurant dates, massages, cultural events, sport activities.’
But he decided to bring it to the attention of the company and sent them a mail.
He soon got a reply from their head of infrastructure and security, asking him to discuss all of it over phone. But Kanishk refused to do that.
“Never have such conversations over the phone. A written correspondence is must ( You’ll have proof in case something goes wrong) I made an excuse & asked him to continue over here or on Facebook.”
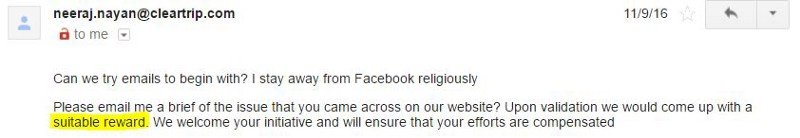
Neeraj Nayan, the man in question, replied saying that he was fine with chatting over emails and that the company was also up for giving Kanishk a reward if his claims were proven.
He responded saying,
He encountered failed transactions too.
“ONE OF THEM WAS AUTOMATICALLY PROCESSED AS ‘MONEY PAID BUT FAILED’. A REFUND REQUEST WAS GENERATED. MY MOBIKWIK WALLET WAS CREDITED WITH 1199 RUPEES.”
Neeraj mailed Kanishk saying that they were validating his claims. But a month into the entire scenario, there was no further correspondence. He even mailed the co-founders, making them aware of the situation.
But to no avail. His efforts went unrewarded and unacknowledged.
But there was no acknowledgment.
He had the power to travel the world for free and no one would’ve even noticed. But his prime concern has been the security of these portals and preventing misuse that can lead to huge losses to these companies. Some acknowledged his efforts, some did not.
What I’ve learnt from my Experiences?
– Indian Companies don’t pay the attention required for security of their Products.
– No Application/Website is entirely secure. Chances are, maybe someone is already exploiting the bugs right under their nose.
– The only way they understand the Importance of Bug Bounty Programmes is through Public Humiliation. Damage control is obligatory once you get hacked. Best Example – Ola Cabs
– Ethical Hacking is rarely appreciated.
– The process of Resolution usually takes a lot of time here. I remember submitting a vulnerability to Mobikwik through their Official Programme. I was just able to Brute Force the OTP during Account Creation. They took like five weeks to get it over with & rewarded me with a sum of 2k ₹.
Full disclosure? I did order a Free Biryani couple of times 😆What surprised me was the fact that no-one from the store manager to delivery boy realised that they were being duped. The first time, I paid in cash after explaining them everything. The second time was a test & they failed again. I could’ve eaten more like a 1000 times.
He informed the company and they soon hired a security firm.
His efforts, rewarded or not, possibly helped these companies upgrade their security.
Air India, SpiceJet, Cleartrip, Mobikwik & Faasos were the only companies I ever corresponded with. Never informed the rest of them about any Loopholes. For the same reason, I never mentioned any technical details in this article. Compromised list may still include some E-commerce websites, Home services, Travel agencies, Educational Institutions, Government applications, etc.